Thinking Outside the Security Blog
Thinking Outside the Security Blog
Check back often for blog posts and news about cyber security and vulnerabilities.
People Security - Behavior Engineering and Information Security
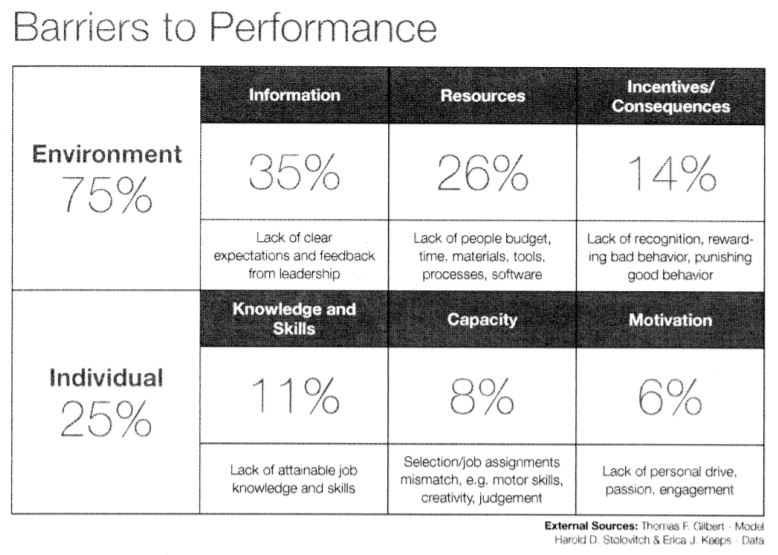
In the last blog articles, I talked about Motivations. In this article, I will talk about the Individual Capacity. As a reminder, the Barriers to Performance is provided below. Note that Individual – Capacity accounts for 8%.
Let’s dive into Individual Capacity. Yet again, I picked another small percentage. What gives? I am purposely discussing the areas people commonly “blame” for issues, but these are less impactful than people think. (Hint: Next blog will be about Individual Knowledge and Skills)
Hold on to your seat. I am going to say some things that will likely make people uncomfortable, or maybe even offend.
Often there is the saying “Wrong person for the job.” This is exactly what this barrier is all about. For Information Security, my opinion is the “right” person is someone who has passion, someone who is willing to put in the extra effort, and someone who is not in it just for the money. The above chart mentions creativity. In Information Security, that is instantiated by “thinking outside the box.” Sadly, I think the industry has produced schools that train people to all think and do the same thing. I have come across too many people in the industry that should be in other jobs. People’s response has been the same for decades to InfoSec problems (a topic for many many other blogs to come). InfoSec is a hard problem, people who are not willing to change or think outside the box will be a mismatch. Lastly, the best match for the InfoSec role is best summed up by a quote from Mike Rothman “…it’s not technical chops that make the best security folks, it’s the attitude and high threshold for pain and frustration.”
I hope this blog article has caused you to “think outside your security box.” Stay tuned for future blogs on Behavior Engineering.
People Security - Behavior Engineering and Information Security
In the last blog article, I talked about Individual Motivation. In this article, I will talk about the Environmental corollary, Incentives and Consequences. As a reminder, the Barriers to Performance is provided below. Note that Environment – Incentives accounts for 14%.
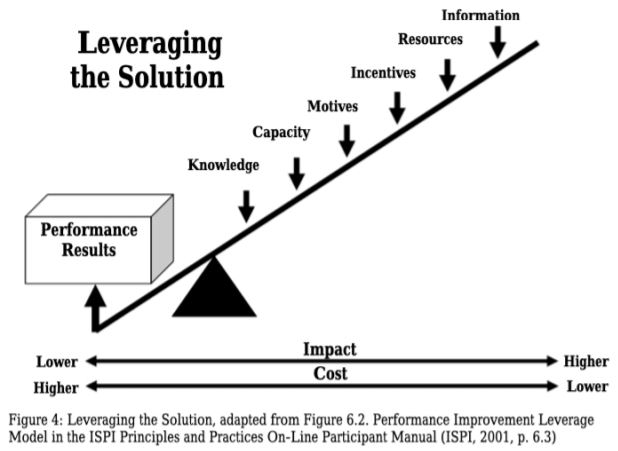
Let’s dive into Environmental Motivation. Wow, I picked another small percentage. However, the updated version of the model shows that Environmental Incentives has more leverage than the Individual Motivation.
How often have you heard that Information Security is a “Thankless Profession” (I am sure there are plenty of other occupations that are this way too). Wow! Talk about lack of extrinsic recognition!! The other well-known concept in security is that no news is good news. Information Security only gets blamed when something goes wrong, but never rewarded for doing 1000 things right that kept you protected for years. Ok. One more example. How many times does the Information Security Professional lament “Why do they not come to us while designing this, they always come right before implementation, and security is ALL WRONG!”
Great, so how do we change this? Environmental barriers mostly boil down to management (Yes, I am pointing to Managers and Executives). Management’s job is to set up the Environment to enable workers to perform. In this case (and many others) the culture needs to be changed. This is no easy task. This takes time.
Let’s discuss the good/bad behavior of allowing things to come to Information Security at the last minute. In order to change culture, you need to communicate the behavior expectation to staff. Once that is done, people need to see that the behavior is easy, rewarding, and normal. You can do two things to make Information Security reviews easy: Make it difficult to get approval or when people engage Information Security early, they get moved to the front of the line. The latter is also rewarding in that they get what they really want, the project is approved instead of stalled by Information Security. The last piece, normal, is more important than the others. Normal means that MOST of the people exhibit the expected behavior. If this doesn’t happen, no matter how easy and rewarding it is, people will not change. While these are not the only solutions, I hope I have planted a seed for you to grow into progress.
I hope this blog article has caused you to “think outside the security box.” Stay tuned for future blogs on Behavior Engineering.
People Security - Behavior Engineering and Information Security
It’s been a while since I wrote my last blog. Life simply has got in the way (or that is the excuse I tell myself). In reality, the problem has to do with lack of resources (time) and motivation (do I do this or have fun/complete HoneyDos).
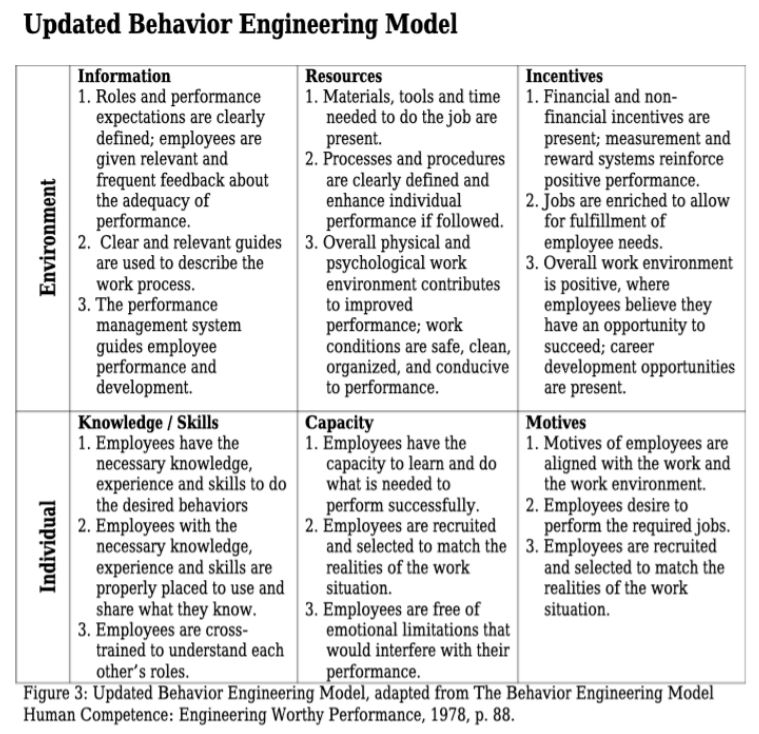
In the last blog article, recall that I stated that the notion of people being the weakest link was misguided. Information Security is still mostly a people problem (yes, there is technology and processes, but who creates those?). If it is a security problem, we need to look at human performance. This blog will introduce you to the Behavior Engineer Model created by Thomas Gilbert in the 1970s.
Gilbert’s model is broken down to two (2) areas: Environmental and Individual (Behavior). Each are further broken down into Information, Instrumentation and Motivation.
In the original model, the Environment accounts for 75% of the barriers to human performance and the Individual accounts for 25%.
In this blog, I will discussion Motives (Individual - Motivation). Why would I pick the smallest percentage category to discuss first? I do this for two reasons: motivation was one of the reasons I have not written a blog in several months, and the problems people commonly attribute to failures (people are the weakest link?) in Information Security are not really what they think. In future blogs, I will relate the remaining five (5) areas to Information Security.
Let’s dive into motivation. While the 6% is small, an updated version of the model shows that individual motivation has more leverage than the other Individual attributes.
As seen by my example, my personal life got in the way of business. Bringing that into the corporate context, think of the end user. Do you think Information Security is #1 on their minds? Did it even break the top 20? The first step is realizing that most workers are not motivated to care about or do anything relating to Information Security. Yes, I know you may “think” this..but have you really accepted it? So what do we do to motivate end users? Start with designing solutions (and use other categories of the behavior engineering model) that allow them to perform their work seamlessly. Another thing you can do is align with what is important to the end user. This typically brings it back to personal life. Have you showed them how this can help both the company and themselves?
I hope this blog article has caused you to “think outside the security box.” Stay tuned for future blogs on Behavior Engineering.
Most Recent Posts ...
Posted on: 6/24/2021
Posted on: 5/20/2021
Posted on: 4/20/2021
Posted on: 2/6/2021
Search All Blog Posts
Blog Post Archives
- People Security - Behavior Engineering and Information Security
- People Security - Behavior Engineering and Information Security
- SolarWinds, cuz everyone else is...
- People Security - Behavior Engineering and Information Security
- The human aspect of Information Security