Thinking Outside the Security Blog
Thinking Outside the Security Blog
Check back often for blog posts and news about cyber security and vulnerabilities.
People Security - Behavior Engineering and Information Security
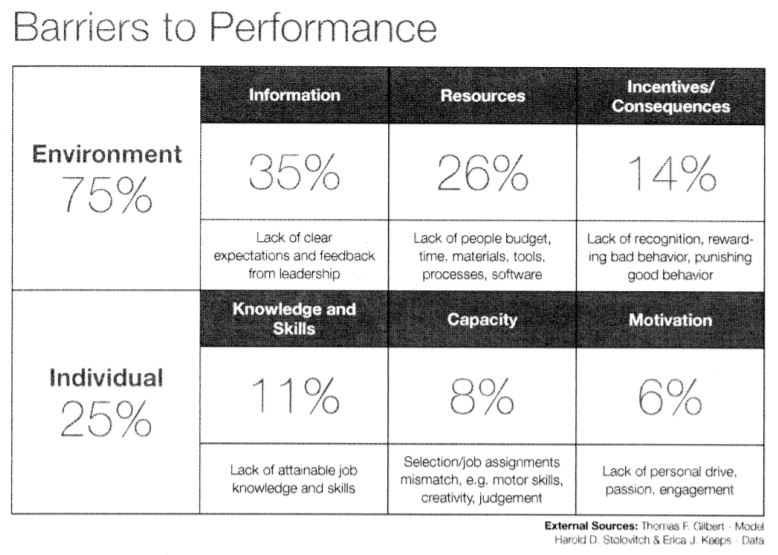
In the last blog article, I talked about Individual Motivation. In this article, I will talk about the Environmental corollary, Incentives and Consequences. As a reminder, the Barriers to Performance is provided below. Note that Environment – Incentives accounts for 14%.
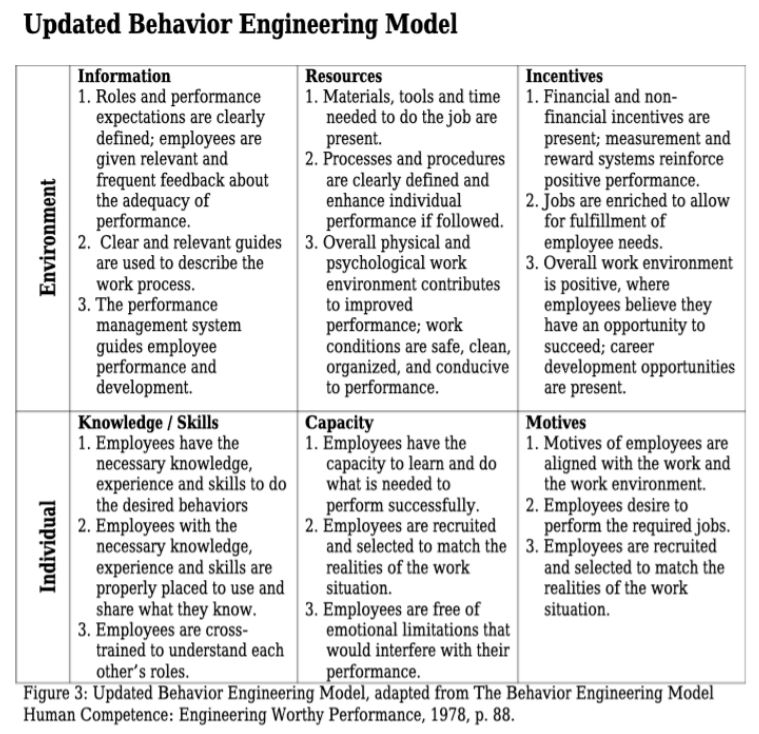
Let’s dive into Environmental Motivation. Wow, I picked another small percentage. However, the updated version of the model shows that Environmental Incentives has more leverage than the Individual Motivation.
How often have you heard that Information Security is a “Thankless Profession” (I am sure there are plenty of other occupations that are this way too). Wow! Talk about lack of extrinsic recognition!! The other well-known concept in security is that no news is good news. Information Security only gets blamed when something goes wrong, but never rewarded for doing 1000 things right that kept you protected for years. Ok. One more example. How many times does the Information Security Professional lament “Why do they not come to us while designing this, they always come right before implementation, and security is ALL WRONG!”
Great, so how do we change this? Environmental barriers mostly boil down to management (Yes, I am pointing to Managers and Executives). Management’s job is to set up the Environment to enable workers to perform. In this case (and many others) the culture needs to be changed. This is no easy task. This takes time.
Let’s discuss the good/bad behavior of allowing things to come to Information Security at the last minute. In order to change culture, you need to communicate the behavior expectation to staff. Once that is done, people need to see that the behavior is easy, rewarding, and normal. You can do two things to make Information Security reviews easy: Make it difficult to get approval or when people engage Information Security early, they get moved to the front of the line. The latter is also rewarding in that they get what they really want, the project is approved instead of stalled by Information Security. The last piece, normal, is more important than the others. Normal means that MOST of the people exhibit the expected behavior. If this doesn’t happen, no matter how easy and rewarding it is, people will not change. While these are not the only solutions, I hope I have planted a seed for you to grow into progress.
I hope this blog article has caused you to “think outside the security box.” Stay tuned for future blogs on Behavior Engineering.
Most Recent Posts ...
Posted on: 6/24/2021
Posted on: 4/20/2021
Posted on: 2/6/2021
Posted on: 2/1/2021
Search All Blog Posts
Blog Post Archives
- People Security - Behavior Engineering and Information Security
- People Security - Behavior Engineering and Information Security
- SolarWinds, cuz everyone else is...
- People Security - Behavior Engineering and Information Security
- The human aspect of Information Security